Back to
[Teams] [Top]
InsidePro Team 2012
Resources
| Active Members
| 20
|
| Names / Nicks
| Admin, blazer, bvv, c0d3inj3cT, dda, Frank89, gscp, h0wler,
jnpe, mastercracker, Mastermind, mr.2x, n00bster, POLIMO,
proinside, raspberry, test0815, Tyra, usasoft, User
|
| Software
| EGB, Passwords Pro, *Hashcat*, John the Ripper, cRARk, AOPR, ARPR, ULM
|
| Hardware
| ~250 CPU cores and 9 GPUs - see individual member writeups
|
Introduction
We would like to begin by giving a big thanks to Korelogic for once
again putting a tremendous effort in organizing the "Crack Me If you
can" contest at Defcon 20, we're sure it wasn't an easy feat. In
addition, we would like to thank "Kaiser" our representative at Defcon
20 and of course every team who participated. While we "Team InsidePro
2012" only placed third, scoring a little over 2 million points, we
would like to acknowledge and congratulate our rivals "Team Hashcat" and
"John-Users" for their marvelous effort in placing first and second
place respectively, both scoring in excess of 3 million points.
This year was a little different as some of the rules were revised and
more challenges were added, in addition these challenges were worth an
exorbitant amount of points. While we understand these new rules were
put in place to give smaller teams a chance to win side prizes, we must
admit this dazed us a little as we were unsure whether solving already
solved challenges would give us points or whether it was a "first come
first serve" basis. This caused a bit of confusion as we debated whether
to solve the harder unsolved challenges or easier already solved
challenges and therefore ignored them completely during the early stages
of the contest until things were confirmed.
Our team
Our team this year comprised of roughly 20 members geographically
scattered around the world with members from (Russia, Australia, United
States of America, Canada, Switzerland, France, Italy, Portugal and
Germany). The software and hardware which we used is shown in Table
1.
| GPU | Count | | CPU | Count | | Software
|
| Radeon 7970 | 8 | | AMD Athlon 64 X2 | 1 | | EGB
|
| Radeon 5770 | 2 | | AMD Phenom 9500 | 1 | | PasswordsPro
|
| Radeon 6950 | 1 | | AMD Phenom 9550 | 1 | | HashcatPlus
|
| Radeon 5850 | 3 | | AMD Phenom X6 1055T | 1 | | John the Ripper
|
| Radeon 5750 | 3 | | Intel Core i5 2500k | 3 | |
|
| Nvidia GTX 470 | 1 | | Intel Core i5 750 | 1 | | cRARk
|
| Nvidia GTX 460 | 2 | | Intel Core i7 2600k | 4 | | UZC
|
| Nvidia GTX 260 | 1 | | Intel Core i7 2600QM | 1 | | AOPR
|
| Nvidia GTX 250 | 3 | | Intel Core i7 620M (MBP) | 1 | | ARPR
|
| Nvidia GTX 550Ti | 1 | | Intel Core2Duo Q6600 | 1 | |
|
| | | | Intel Core2Duo Q9400 | 2 | | Hashcat Utils
|
| | | | Intel Pentium E5200 | 1 | | ULM
|
| | | | Intel Xeon 5130 | 2 | |
|
| | | | Intel Xeon 5365 | 2 | |
|
Table 1. A rough list of our hardware and software capabilities. Note: Not all software/hardware listed was used continuously throughout the 48 hour period.
Approach
As usual, we took the more relaxed approach and once again adopted the
free-for-all tactic. This allowed each member to attack whatever hash
type they preferred, the results would then be collated, parsed and then
submitted. We, as a team, decided that it would be best to initially
recover as many passwords as possible, analyze the passwords and look
for patterns and perhaps `fingerprinting' them for our secondary
attack.
The Game
Unlike other teams which appeared to have raced for the challenges, we
largely ignored them until several hours into the contest when different
solutions to the challenges were submitted and we realized from the
stats page that there were actually points being credited for solved
challenges.
We noticed some of hashes required reformatting to make them compatible
with EGB, ppro and the hashcats and this was carried out swiftly by
various team members. We were surprised with the new addition of sunMD5
and dynamic 21, but we did our best to recover hashes from these
algorithms.
After many hours of different attacks we saw certain patterns emerge and
these included the use of lists from Swiss Cities, Greek Names, other
patterns included but not limited to are; pure numeric, dates and
strange dates, some heavy passwords reuse such as `password' and
`dealtime' in their permuted forms to name a few. The team then started
to run various attacks with a focus on these lists in an attempt to
exploit these patterns. While this technique worked, we realized it was
not ideal to perform on the extremely resource intensive algorithms such
as Blowfish, mscache2, md5(APR) etc. In addition from our `cracks' we
could not see a clear pattern in these slow algorithms besides them
being common words. It was only late on day 1 towards day 2 that we had
some significant breaks for tougher algorithms and also DES(Unix).
Through the competition, we largely remained within the top 3 positions,
mainly trading places with "Team Hashcat" and "John-users". While we
expected other teams to hang on to batches of high scoring hashes as a
safety net, our general team consensus was that we would submit
everything we had. This worked quite well, as it baited other teams to
show their true colors, making them submit what they had to remain top
dog... or cat.
Towards the end of the contest, we were really in bind, we realized
there were only 2 ways to be able to obtain a good score 1) Focus only
on the toughest algorithms or 2) Attempt to score the bonuses from
cracking as many hashes as possible for the various easier algorithms.
In order to boost our score our team had to alter our carefree approach
and instead we all focused solely on the tougher algorithms.
Breakthroughs
DES(UNIX)
We noticed a fair few passwords were blocks of sentences and phrases,
meaning bruteforce attacks would be futile on the hashes. We instead
gathered text which fit this profile and applied the following `recipe'
on them to produce some nice working lists which we could just use for
direct dictionary attacks.
An example of what we used for DES(Unix):
- Input slab of text/wordlist
- Substring out text with minimum length 8+
- Line Tools > Remove if line only contains > Digits
- Downsize > Save if length is 8
- Sort > Sort and Remove duplicates
Blowfish
Several members noticed that dinosaurs were a common theme in the
passwords we recovered and some of the toughest algorithms contained a
couple of hits with this property. All efforts were then directed
towards hitting these algorithms namely Blowfish with these
wordlists.
MD5 crypt, MD5 APR
Many of the passwords which were cracked appeared to be lower alpha
varying from 8 to 10 characters long. In addition, there were many
passwords with the titled property (First Character Upper, Lower case
rest)
Some rough statistics from our teams' password haul
Our team recovered passwords with lengths exceeding 20 characters (not
shown). Figure 1. suggests that a large proportion of passwords that we
were able to recovered were predominantly length 9. Figure 2. shows that
we were able to recover large portions of the lower-space and
mixed-alpha space styled passwords.
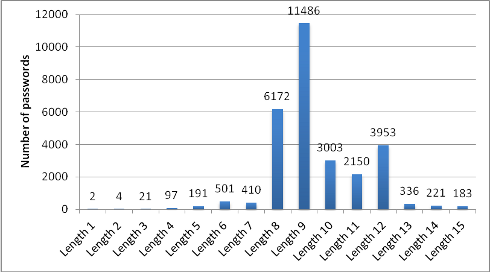
Figure 1: Length of the recovered passwords cracked by Team InsidePro (truncated to length 15)
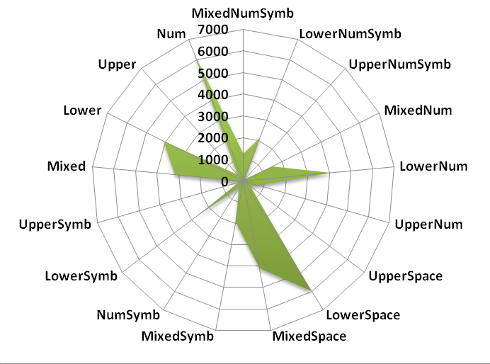
Figure 2: istribution of the recovered passwords by character set, cracked by Team InsidePro (partial)
Reflection, comments and suggestions
In contrast to some of the larger teams we were probably under geared,
coupled with our carefree approach, this seriously put us at a
disadvantage as we weren't using our hardware efficiently. While we
should work on our team dynamics better, the important thing is that it
was a great challenge and it was a pleasure to participate once
again.
We expected the passwords to resemble more of a password leak, however
they appeared to be more methodically generated. This is understandable,
as there is only so much variation that can be used before all mangling
rules are exhausted. We will have to reconsider both our approach and
our attack methodology to better suit this sort of password
selection.
Our major downfall would be the fact that we, unlike John-Users, didn't
focus on the higher scoring algorithms enough. However despite our 3rd
place in overall points, our team was able to crack the second highest
number of hashes, suggesting that the problem was attributed to
execution rather than the technique we used in recovering the
passwords.
We would like to thank Korelogic for the addition of new challenge types
which made it very interesting, we would also look forward to WPA/WPA2
hashshakes, if that was thrown into the mix. We largely agree with the
weighting of the points for the different algorithms. However, while we
understand that DCC2 can be accelerated with GPU, we believe it deserves
a higher scoring value due to its computing requirements.
Some team members have suggested to move the contest to the weekend
(Saturday/Sunday), as we had a fair few late comers in our team this
year. We do understand though, that there are many people participating
from all over the world in different time-zones making it impossible to
cater for everyone. Another suggestion would be to issue personalized
certificate / diploma for all team members of the top 3 teams. It could
have a couple of logos like Defcon, Korelogic, etc. and state the team
member name, the team name and the ranking.
While we acknowledge these issues may have had little or no effect on
our team, we would like to voice some minor complaints about the
contest. For starters the rules of the contest should be better
clarified, as stated previously we were confused with how the scoring of
the challenges worked. Additionally we expected the release of the PGP
password to be delivered through email rather than on the website. It
also appeared that the hash bonus was modified from 100k to 50k during
the contest as we kept a close eye on the stats page.
Once again we would like to thank Korelogic for organizing 'Crack me if
you can'. We would also like to thank those who have read up to this
point in our write-up. If you have further questions or any queries, do
not hesitate to join us in a discussion at
http://forum.insidepro.com.


