Back to
[Teams] [Top]
Team hashcat
Resources
| Active Members
| 19
|
| Nicks
| atom, d3ad0ne, radix, hbpanda, superjames, dakykilla, Xanadrel, K9, blaz,
pure_hate, blandyuk, Rolf, kartan, RuraPenthe, |m|, chancas, ToXiC, iphelix,
unix-ninja
|
| Software
| oclHashcat suite, disthc, custom scripts, Passcovery Suite, John the Ripper
|
| Hardware
|
83+ CPU cores (+ some hyperthreads), 54 GPUs
|
Summary
The initial feeling this year was that the contest had become overly
complicated. The KoreLogic team introduced several new rules which
seemed designed to handicap the larger teams, while we definitely
appreciate the idea of getting more people involved in password
cracking, as a large team, we felt rules such as those to be biased.
Additionally, this year we did not feel the passwords and hash types
were an accurate reflection of real world situations. Most of us as
security professionals, have tools and mindsets that are crafted to
attack hashlists which we find on penetration tests or publicly released
list. For example the average length of the passwords this year was 21
characters (See: CrackMeIfYouCan
Twitter Status) which is contrary to all data from recent breaches.
Statistically the average password length is eight (8) characters. There
was also no underlying theme to the passwords as there were in previous
years, this goes against what is seen in most password breaches. After
some time it became obvious that passwords where just sentences from
books which unrealistic. This year's contest also seemed to be keeping
with the theme of favoring John the Ripper as all algorithms were
supported by this tool, which can't be said for Hashcat and
PasswordsPro.
We would like to extend our thanks to KoreLogic for taking the time and
effort out of their otherwise busy work schedules to facilitate this
contest. While we did have a few complaints this year, we do realize the
substantial amount of effort that goes into creating a contest of this
magnitude. We imagine that making this appealing to a wide range of
individuals can be challenging and again we appreciate KoreLogic taking
the time to put this together. In the past KoreLogic has always been
receptive to contest feedback and we can only assume the same will be
true for this year. As always we had a good time competing and the level
of effort all of the teams put into the contest was amazing. The Hashcat
team loves competition and is looking forward to next year's contest.
Contest Breakdown
Initially we started the contest in a similar fashion to previous years.
We set out to crack as many passwords as we could by applying wordlists
with common mutations. After the initial batch of easy hashes was
cracked, the team regrouped and analyzed the current plains to determine
a pattern or common theme. In previous competitions, KoreLogic had
generated passwords by mutating plains in common ways seen in industry
breaches. This year however plains where mostly generated by using
phrases from a wide range of books, novels, and screenplays. This put us
at a disadvantage, as we weren't able to employ techniques such as
Markov attacks, or rule mutations commonly used for attacking passwords.
This also left some of us in a moral dilemma as we would essentially
have to pirate authors works to obtain phrases and words that we needed.
Disappointed, the team set off to download parts of novels, and text
from the Internet and reconstruct phrases that would be used as flat
dictionaries. We quickly identified clues which books were used (Lord of
the Rings Trilogy, Pride and Prejudice, and others). Atom created some
scripts which helped us to create the pass phrase dictionaries. They can
be downloaded here:
http://hashcat.net/CMIYC2012/phraser1.pl
http://hashcat.net/CMIYC2012/phraser2.pl
Several other lists the Hashcat team used can also be downloaded:
http://hashcat.net/CMIYC2012/dates
http://hashcat.net/CMIYC2012/ip_left
http://hashcat.net/CMIYC2012/ip_right
http://hashcat.net/CMIYC2012/cities.txt
http://hashcat.net/CMIYC2012/password.dic
Some rules:
http://hashcat.net/CMIYC2012/insert_overwrite.rule
http://hashcat.net/CMIYC2012/npass.rule
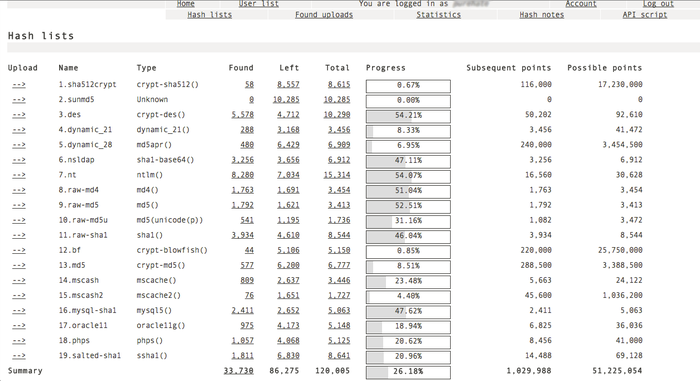
Thanks to superjames, hash types were organized and loaded into a
homegrown management system dubbed "List Condense", coded specifically
for this competition. Recovered plains were uploaded to the website
where they went through a quick verification process, and if passed,
removed from the list and added to a dictionary. Recovered hashes,
remaining hashes, and plaintext dictionaries were all updated in
real-time. Members were able to download left hashes easily to minimize
work being duplicated.
Rolf bossed the challenges right away, putting us up a quick six (6) in the
first hour of the CMIYC contest. Custom scripts, no matter how good, will
never do that. The software he used to crack 6 of the challenges is called
Passcovery Suite, coded by a brilliant russian known as IvanG. It's very
optimized and has built-in attacks, which brought us success, along with a
private wordlist. This was then knocked back down to 4 due to a PGP key
submission error.
Once everything was sorted we were sitting happily with four (4) first cracks,
and most of the hashes in List Condense application ready to be worked. The
team quickly rose to the top banging out the easy stuff and identifying sources
to use as lists. Unix-Ninja had also been working on a server/client solution
for distributed cracking (disthc) which allowed us to queue sessions, by
distributing the work load, and dictionaries via the Internet.
It would seem KoreLogic tried to even the odds between teams by
introducing an obscure algorithm sun-md5, in addition to weighing
heavily on bcrypt and sha512crypt. We had an ace up our sleeve though,
as atom had added both bcrypt and sha512crypt to a non-public version of
oclHashcat-plus prior to the start of the competition. Radix and d3ad0ne
used their larger GPU powered machines to focus efforts on these hash
types. This worked amazingly well until we started seeing passes greater
than 15 characters at which point we were forced to fall back to CPU's
due to a limitation in oclHashcat-plus of fifteen (15) characters. The
other high scoring hash type was sun-md5 which many of us had never even
seen. This put us in a bit of a bind being worth 3000 points each,
thankfully iphelix threw together a cracker in python and away we went
slowly applying our word lists. For the most part, we didn't even bother
with these as it was apparent that bcrypt, sha512crypt, md5crypt were
going to be what won the most base points. Iphelix generated some rules
using rulegen.py which will ship with the next PACK release. The new
tool uses the Levenshtein-distance algorithm to automatically generate
rules or better said, to regenerate rules. This way we thought if we
only know the source (Dictionary) that KL used and that was later
mutated using rules like it was in the last years we can regenerate the
rules KL used and regenerate the full plain list.
Deciding to employ a bit of PsyOps, we held back some of our high value
hashes to see if someone would do a big submit to take the lead. Inside
Pro was first to bite and join us. All three (3) teams played cat and
mouse with uploads for a while then we dropped the bomb. This gave us a
comfortable lead, but all good things come to an end. The John-Users and
Inside Pro submissions started adding up and we were hitting walls
trying to figure out how phrases had been cut out of the books. Down to
the last thirty (30) minutes got pretty hairy. Inside Pro appeared to
have hit a wall and the JTR team was trickling plains in slowly
overtaking us in raw points. Down to the last ten (10) minutes it was
just a question of JTR having enough cracks to take the bonus points. We
pushed our last submissions and powered down to see how KoreLogic scored
it.
| Name | CPUs | GPUs | OS
|
| atom | AMD FX8120 | AMD hd6990 | Ubuntu 12.04 x86_64
|
| blandyuk | AMD FX8120 | AMD hd5850 | Win 7 x64
|
| blaz | i7 | 2x AMD 7970 | Win 7 x64
|
| chancas | i7 | 2x AMD 7970 | Win 7 x64
|
| d3ad0ne | i7 980x, 2x Xeon x5650 | 4x ATI 6970, 8x ATI 7970 | Ubuntu 12.04 x86_64
|
| hbpanda | AMD FX6100 | AMD 5870 | Ubuntu 12.04 LTS
|
| iphelix | unknown | unknown | unknown
|
| k9 | i5 2500K | ATI 6970 | Win7 x64
|
| radix | 2x Xeon 5645, i7 3770K | 7x Nvidia 580 GTX, 2x AMD 7970 | Ubuntu 12.04 x86_64, Windows 7 x64
|
| Rolf | FX-8150 | 2x NVidia 480 GTX | unknown
|
| superjames | i7 | 4x ATI 6990 GPU donated by Ranvik | Debian x64
|
| T0XlC | Xeon E5502 | ATI 5870 | Win7 x64
|
| xanadrel | i7 3820, i3-2130 | 2x ATI 7970 | Win7 x64, Ubuntu 12.04 x86_64
|
| |m| | unknown | unknown | unknown
|
| dakykilla | 2x AWS XL, unknown | 2x ATI 6990 | Cent OS 64 bit
|
| pure_hate | unknown | 8x Nvidia 580 GTX | Ubuntu 11.10
|
| RuraPenthe | unknown | unknown | unknown
|
| dropdead | AMD X2, i7 920 | AMD 5970, Nvidia 570 GTX | Ubuntu 12.04 x86_64
|

